So you think you need a SOC?
For most SMBs, building an in-house SOC is complex and costly. Automated detection and response from Blumira is what you need.
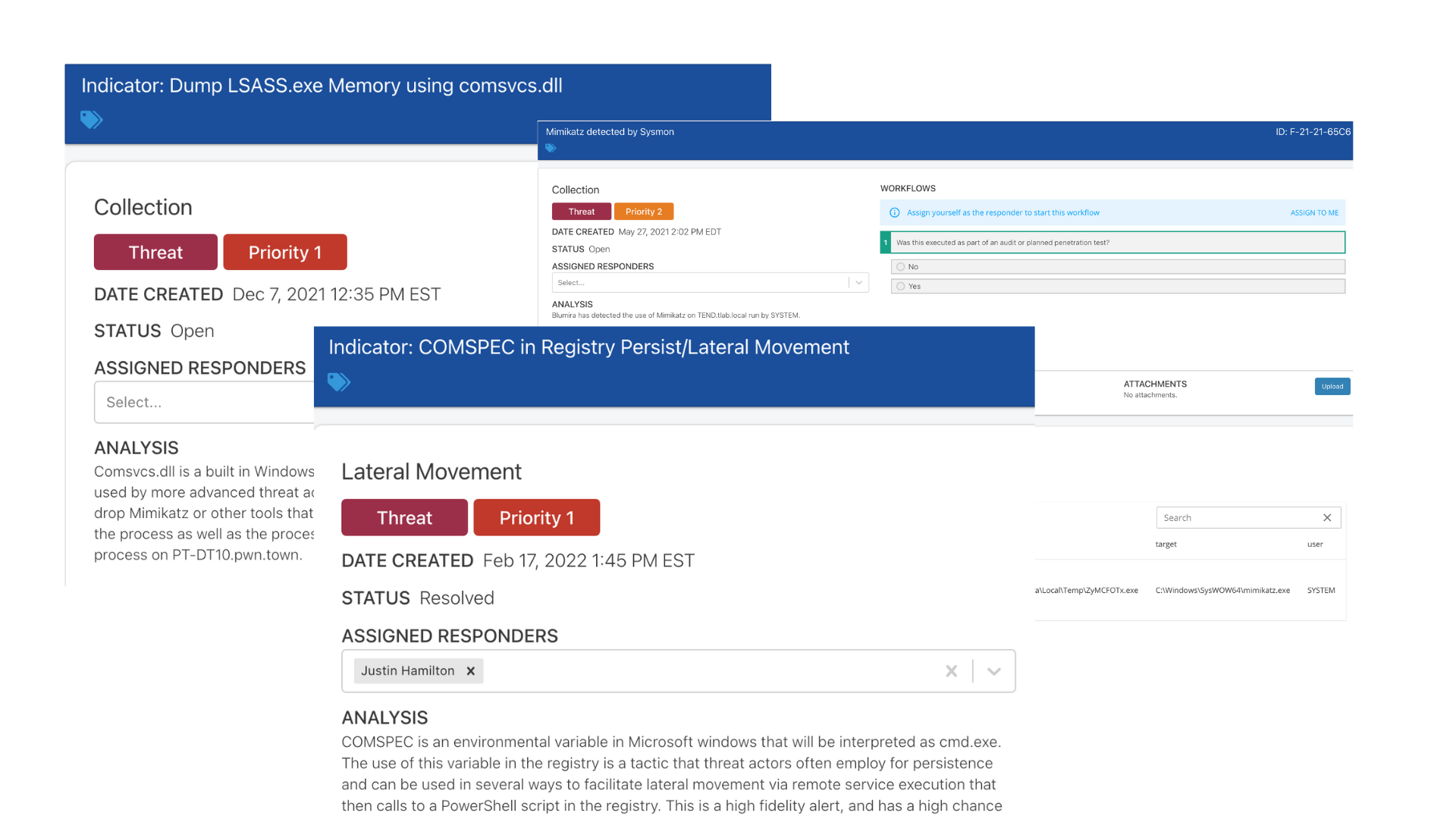
Read MoreUncover Threats in Your Windows Environment with Sysmon
Sysmon provides critical visibility into Windows systems activity. Learn how it works and why you need it in this comprehensive guide.
Read MoreWhy You Should Migrate From On-Premise Exchange
Migrating from on-prem exchange can be a daunting task. See why it's important based on recent attacks, vulnerabilities, and best practices.
Read MoreIncident Response Steps for State and Local Governments
Learn key incident response steps and NIST incident response strategies for enhancing government cybersecurity effectively.
Read MoreAce the State and Local Cybersecurity Grant Program Application—Without Going Crazy
Learn what key strategies can help IT teams ace the state and local cybersecurity grant program application.
Read More4 Unexpected Ways to Strengthen State and Local Government Cybersecurity
Discover 4 strategic steps designed for IT Directors to build robust local government cybersecurity plans.
Read MoreHow to Identify and Prevent Phishing in Businesses
Learn about the most common signs of phishing attacks and how IT teams can educate employees on preventing them.
Read MoreHow Leaders Can Foster a Culture of Cybersecurity
Protecting an organization from cyberattacks starts at the top. Here’s how leaders can develop a culture of cybersecurity.
Read MoreCybersecurity Detection and Protection—No Matter How You Say it
Is it "seem" or "sim"? The cybersecurity community is divided on how to pronounce the acronym SIEM. While there's no consensus yet, one thing we can agree on is that SIEM solutions like Blumira's are essential for automated threat detection, protection, response and compliance - regardless of how you say it!
Read MoreHow to Get Cybersecurity Buy-in from Executive Leadership
Learn how to frame your cybersecurity needs in a way that gains executives’ trust and collaboration for adopting new strategies, processes, and solutions.
Read More