6 Tips for a Remote Working Security Policy
Remote work can introduce risks, which is why an effective remote work security policy is important. Learn the best practices for developing a strategy.
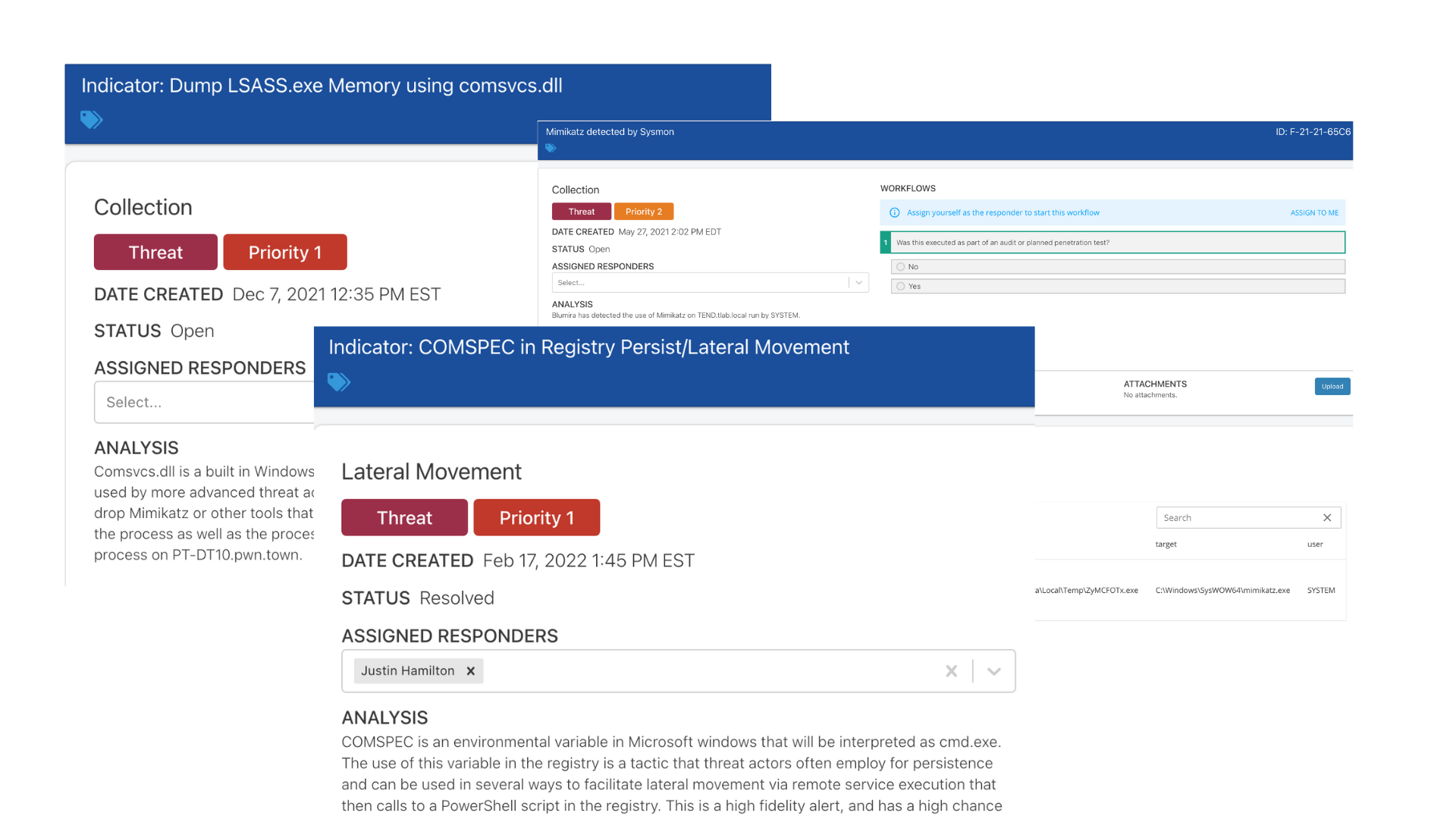
Read MoreHow To Detect SYSVOL Enumeration Exploits
Attackers can gain unauthorized access to the domain via a SYSVOL exploit. Learn ways to detect these exploits and stop an attack in progress.
Read MoreMonitor Remote Employees Ethically and Effectively
Remote employee monitoring has a bad rap, but there's a way to get it right. Here are tips on how to remote work successfully and ethically.
Read More5 XDR Features Small Businesses Should Prioritize
Not every XDR vendor is a good fit for small businesses. Take a look at XDR features that SMBs and small teams should prioritize.
Read MoreTop Help Desk Tools 2023: Choose the Best for Your Needs
Use our list of the ten best help desk tools and best practices to begin the journey to excellent, scalable customer service.
Read MoreAssessing Your Firewall Needs for Enhanced Security
Firewalls still play essential roles in keeping networks and devices secure. To understand why you need a firewall, it's important to know how they work.
Read MoreHow Endpoint Isolation Locks Down Cyber Attacks
By isolating the infected endpoint, you can interrupt attack chains and prevent lateral movement of attacks. Learn more about endpoint isolation here.
Read MoreTop 5 Steps For SMB Endpoint Security Success
5 steps small to mid-sized businesses (SMBs) can do to stop the flood of endpoint security issues, while focusing on the day-to-day of their business.
Read MoreWhat Are Event Logs and Why Do They Matter?
Analyzing logs helps with the technical support of devices, users, applications, and more. Learn more about why event logs are so important.
Read MoreHow To Manage Windows Firewall with GPOs
Managing Windows Firewall with Group Policy is easier and faster. Here’s a step-by-step tutorial of how to configure Windows Firewall with GPOs.
Read More