Comprehensive Cybersecurity,
Simplified for Your Team
- Cybersecurity in just 15 minutes a day
- Defend against ransomware
- Easily meet compliance requirements
- Managed backend, 24/7 monitoring, automated response
Trusted by Companies Like Yours
Blumira proudly serves industry leaders, providing security and support for businesses of all sizes.

















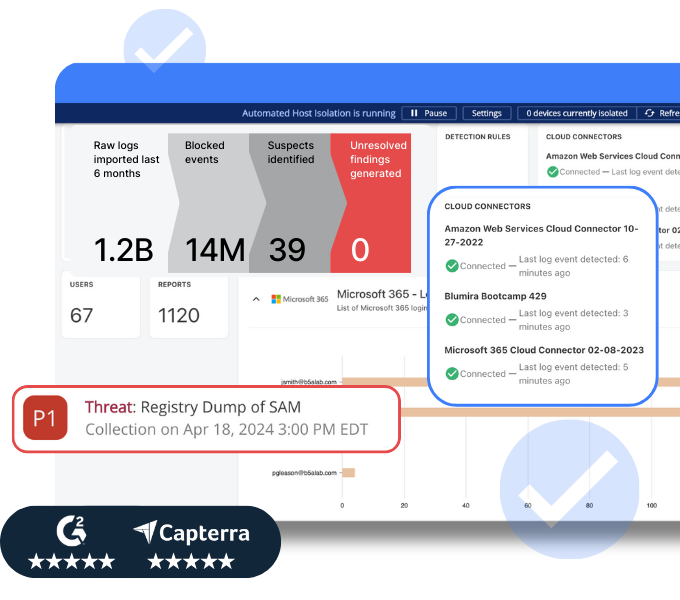
The SIEM + XDR Solution That Simplifies Security for IT Teams
Blumira turns complex security into a simple, swift, and stress-free experience, giving you the freedom to focus on what matters most.


.png?length=720&name=HOME%20-%20UPDATED%20EndPoint%20-%20LG%20(1).png)

A Proven Effective Solution
Easily Meet Compliance Frameworks
Blumira simplifies meeting key compliance and cyber insurance requirements with quick deployment, pre-built compliance reports, 24/7 monitoring, and 1 year data retention.
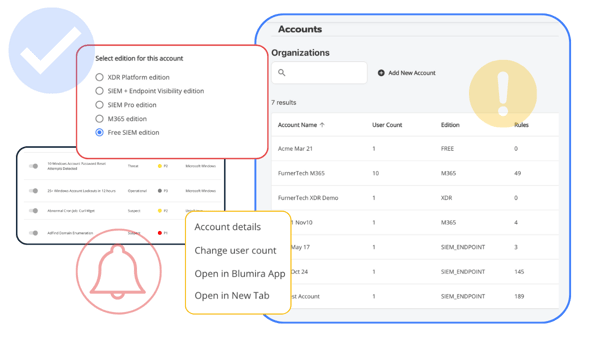
SIEM Made Easy for MSPs
Blumira enables MSPs to protect their customers with faster detection and response while meeting requirements for cyber insurance and compliance frameworks. Blumira makes security simple to manage and affordable for SMBs. Blumira is free for MSP internal use through NFR licensing.
Become a PartnerEffective Security for Industries That Need It
We strive to make cybersecurity feel less like a burden, acting as a trusted partner across a wide range of applications.
-
Healthcare
Healthcare
Beyond supporting HIPAA compliance, Blumira helps secure patient data, detect common healthcare attacks and address security challenges, so you can focus on health, not hacks.
-
State and Local Government
State and Local Government
Municipalities and agencies deserve world-class protection without the need for additional resources. Guard against threats and check off compliance boxes without the headaches.
-
Financial Services
Financial Services
Financial sector security without the financial headache. Achieve compliance and counter threats with a solution that fits your needs and your budget.
-
Manufacturing
Manufacturing
Build stronger, safer. Meet ISO 27001 effortlessly and protect your production lines from cyber threats with our easy, effective security solution.
-
View All Industries
View All Industries
We support all industries to bring them our powerful cybersecurity solution without requiring additional security resources.
Healthcare
Beyond supporting HIPAA compliance, Blumira helps secure patient data, detect common healthcare attacks and address security challenges, so you can focus on health, not hacks.
State and Local Government
Municipalities and agencies deserve world-class protection without the need for additional resources. Guard against threats and check off compliance boxes without the headaches.
Financial Services
Financial sector security without the financial headache. Achieve compliance and counter threats with a solution that fits your needs and your budget.
Manufacturing
Build stronger, safer. Meet ISO 27001 effortlessly and protect your production lines from cyber threats with our easy, effective security solution.
View All Industries
We support all industries to bring them our powerful cybersecurity solution without requiring additional security resources.
In Their Own Words
Hear directly from our partners and customers how Blumira has transformed their cybersecurity posture.
“We’re required by CJIS and IRS Pub 1075 compliance to review our logs daily. Blumira has saved us time because we can’t monitor all of our logs — we would need a team of 100 to go through all of these logs manually.”
Mike Morrow
Technical Infrastructure Manager, Ottawa County
“The team has a lot to do with my satisfaction...your entire support team has been awesome. They are willing to go out of their way for you. Blumira is at the top of the list when it comes to customer support.”
Frank DeLuca
President, The CTO Agency
“If anything pops up, your support team has been fantastic. I can’t say enough great things. They are very responsive, genuine, and understanding. Even if it’s something on my side, they are still willing to lend a hand. That means a lot.”
Christopher Reddekopp
Level 2 Support, Tullahoma Utilities Authority
Get Started for Free
Experience the Blumira Free SIEM, with automated detection and response plus compliance reports for 3 cloud connectors, forever.