Industrial (ICS/OT) Cybersecurity
Internet-connected industrial control systems (ICS) and operational technology (OT) are common targets for attackers seeking to steal data or disrupt operations. These systems monitor critical infrastructure and complex industrial processes that operate power grids, transportation, manufacturing and other services.
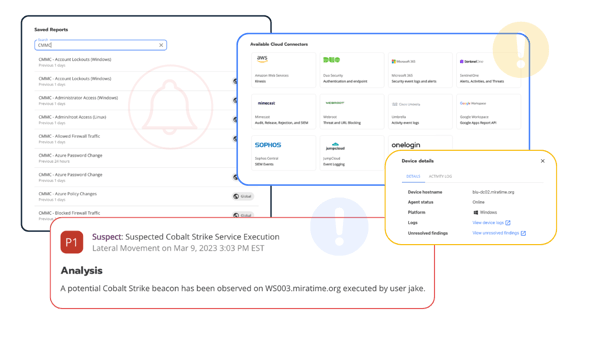
OT Security Challenges
The industrial sector faces certain key challenges that when it comes to securing industrial or OT infrastructure:
- A shortage of talent with ICS cybersecurity expertise
- Lack of overall security visibility and asset inventory/discovery
- Inability to detect risks or threats across connected systems
- Increasing connectivity of ICS to enterprise networks and the internet across operational technology (OT), exposing them to risk
- Requirements to keep all key systems running, despite legacy use of insecure protocols or end-of-life equipment (no longer supported by vendors)
Best Practices for Securing OT Infrastructure
-
Centralizing the view into activity across complex, interconnected, and distributed systems using a SIEM (security information and event management) system
-
Automating the collection, parsing, analysis, and correlation of log data from key systems to monitor for anomalies and early indicators of an attack
-
Detecting the use of insecure protocols or common misconfigurations that can broaden the attack surface
-
Keeping event logs and historical data, with search and reporting capabilities to help with deeper investigation, detection, and response
-
Responding to events quickly using gathered evidence and guided security playbooks for next steps in order to contain or block threats
-
Pair SIEM (security incident and event management) with automated detection and response in one solution to reduce integration complexity, address solution sprawl, and save time spent switching between tools
Common Security Issues Seen in Industrial Attacks
How Industrial Organizations Detect Cyber Attacks With Blumira
Blumira offers an all-in-one solution for industrial companies to help detect and respond to threats and prevent a ransomware attacks and data breaches
Blumira for Industrial Control Systems
Five ways Blumira makes cybersecurity easy for industrial operations
-
Ease of Deployment & Use
Ease of Deployment & Use
Set up Blumira’s cloud-delivered detection and response platform in minutes or hours, using your existing team - no need for security expertise to manage or respond to alerts. -
Lower TCO (Total Cost of Ownership)
Lower TCO (Total Cost of Ownership)
On average, Blumira is 25-40% more affordable than other SIEM providers, making it easy to justify budget and ROI (return on investment) to your executive board. -
Automated Security Operations
Automated Security Operations
The Blumira platform automates threat hunting and analysis. Using pre-built rules, Blumira sends high-value alerts on detected threats so small teams know what to prioritize and how to respond. -
Comprehensive Coverage
Comprehensive Coverage
Out-of-the-box, vendor-agnostic integrations with third parties across on-premises and cloud applications provide advanced security visibility and wide coverage across complex, hybrid environments. -
Trusted Security Advisors
Trusted Security Advisors
You get access to responsive, helpful security advice from Blumira's in-house security operations team. We'll assist with onboarding, management, new integrations, or incident response triage and investigation as needed - acting as an extension of your existing IT team.
Ease of Deployment & Use
Set up Blumira’s cloud-delivered detection and response platform in minutes or hours, using your existing team - no need for security expertise to manage or respond to alerts.Lower TCO (Total Cost of Ownership)
On average, Blumira is 25-40% more affordable than other SIEM providers, making it easy to justify budget and ROI (return on investment) to your executive board.Automated Security Operations
The Blumira platform automates threat hunting and analysis. Using pre-built rules, Blumira sends high-value alerts on detected threats so small teams know what to prioritize and how to respond.Comprehensive Coverage
Out-of-the-box, vendor-agnostic integrations with third parties across on-premises and cloud applications provide advanced security visibility and wide coverage across complex, hybrid environments.Trusted Security Advisors
You get access to responsive, helpful security advice from Blumira's in-house security operations team. We'll assist with onboarding, management, new integrations, or incident response triage and investigation as needed - acting as an extension of your existing IT team.Additional Security Resources
View All Posts
Webinar 7/17: Better Signal, Less Noise With New API and Detection Filter Enhancements
Read More
New Detection: Catching Session Token Theft in Microsoft 365
Read More
Blumira Detections: Reduce Noise & Improve Your Time to Respond
Read MoreGet Started for Free
Experience the Blumira Free SIEM, with automated detection and response plus compliance reports for 3 cloud connectors.