SIEM + XDR for State and Local Government
Safeguarding valuable data against rising threats with limited resources is easier said than done. Empower your government municipality or agency with easy, effective cybersecurity from Blumira.
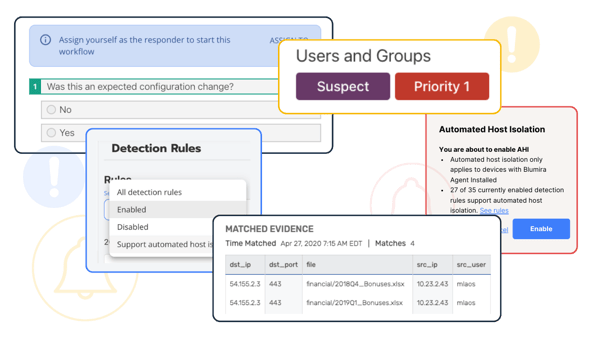
Securing Government Networks Is What We Do
"We’re required by CJIS and IRS Pub 1075 compliance to review our logs daily. Blumira has saved us time because we can’t monitor all of our logs — we would need a team of 100 to go through all of these logs manually."
Mike Morrow
Technical Infrastructure Manager
Key Advantages For Local Governments
Blumira provides comprehensive security solutions tailored to the unique needs of state and local governments to ensure compliance, efficiency, and robust protection.




Our Features
Discover how Blumira uniquely supports state and local governments.
-
Compliance
Compliance
Ensure CJIS standards are met with our out-of-the-box SIEM. Blumira provides capabilities for generating audit records, logging system events, automating the audit monitoring and analysis process, retaining audit logs for one year, and more. -
Ready-Made
Ready-Made
Deploy Blumira pre-configured detections for common government threats quickly to ensure immediate protection. -
Unparalleled Support
Unparalleled Support
Gain peace of mind with our 24/7 SecOps team. We’re always ready to assist with any critical security issues.
Compliance
Ensure CJIS standards are met with our out-of-the-box SIEM. Blumira provides capabilities for generating audit records, logging system events, automating the audit monitoring and analysis process, retaining audit logs for one year, and more.Ready-Made
Deploy Blumira pre-configured detections for common government threats quickly to ensure immediate protection.Unparalleled Support
Gain peace of mind with our 24/7 SecOps team. We’re always ready to assist with any critical security issues.How We Empower Your Security
Dive into how we turn complex security challenges into manageable, everyday victories for local and state governments.
Read up on the Latest Insights
View All
NIST Cybersecurity Framework Implementation for Mid-Market Companies: 2025 Update
Read More
Customer Story: District of Sparwood
Read More
Security expert Nick Brigmon discusses Florida’s new cybersecurity standard bill
Read MoreGet Started for Free
Experience the Blumira Free SIEM, with automated detection and response plus compliance reports for 3 cloud connectors.