- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
What Is Cloud Security Monitoring?
Cloud security monitoring is the practice of continuously supervising both virtual and physical servers to analyze data for threats and vulnerabilities. Cloud security monitoring solutions often rely on automation to measure and assess behaviors related to data, applications and infrastructure.
How Does Cloud Security Monitoring Work?
Cloud security monitoring solutions can be built natively into the cloud server hosting infrastructure (like AWS’s CloudWatch, for example) or they can be third-party solutions that are added to an existing environment (like Blumira). Organizations can also perform cloud monitoring on premises using existing security management tools.
Like a SIEM, cloud security monitoring works by collecting log data across servers. Advanced cloud monitoring solutions analyze and correlate gathered data for anomalous activity, then send alerts and enable incident response. A cloud security monitoring service will typically offer:
Visibility. Moving to the cloud inherently lowers an organization’s visibility across their infrastructure, so cloud monitoring security tools should bring a single pane of glass to monitor application, user and file behavior to identify potential attacks.
Scalability. Cloud security monitoring tools should be able to monitor large amounts of data across a variety of distributed locations.
Auditing. It’s a challenge for organizations to manage and meet compliance requirements, so cloud security monitoring tools should provide robust auditing and monitoring capabilities.
Continuous monitoring. Advanced cloud security monitoring solutions should continuously monitor behavior in real time to quickly identify malicious activity and prevent an attack.
Integration. To maximize visibility, a cloud monitoring solution should ideally integrate with an organization’s existing services, such as productivity suites (i.e. Microsoft 365 and G Suite), endpoint security solutions (i.e. Crowdstrike and VMware Carbon Black) and identity and authentication services (i.e. Duo and Okta).
Learn More About Blumira’s Cloud Security Monitoring >
Cloud Security Risks
Cloud environments come with different security risks than traditional on-premises environments. Some common cloud security threats include:
Misconfigurations. Human error — or failing to set the right security controls in a cloud platform — is one of the biggest cloud security threats. Examples of misconfigurations include accidentally allowing unrestricted outbound access or opening up access to an S3 bucket. Cloud misconfiguration can be extremely damaging; one real-life example of this was the Capital One breach in 2019, in which a former Amazon employee was able to expose personal records of Capital One customers due to a misconfigured web application firewall (WAF).
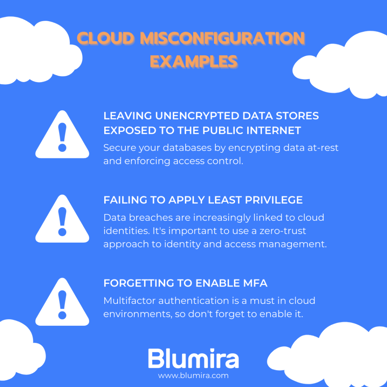
Data loss. The collaboration and shareability of cloud services are double-edged swords; these benefits often make it too easy for users to share data with the wrong internal parties or external third-parties. 64% of cybersecurity professionals cited data loss and leakage as a top cloud security concern, according to Synopsys’ Cloud Security Report.
API vulnerabilities. Cloud applications use APIs to interact
with each other, but those APIs aren’t always secure. Malicious actors can launch denial-of-service (DoS) attacks to exploit APIs, allowing them to access company data.
Malware. Malware is a real threat in the cloud. Data and documents constantly travel to and from the cloud, which means that there are more opportunities for threat actors to launch malware attacks such as hyperjacking and hypervisor infections.
IAM complexity. Identity and access management (IAM) in a cloud or hybrid cloud environment can be extremely complex. For larger organizations, the process of simply understanding who has access to which resources can be time-consuming and difficult. Other IAM challenges in the cloud include ‘zombie’ SaaS accounts (inactive users), and improper user provisioning and deprovisioning. Hybrid environments where users must access a mix of SaaS apps and on-premises applications can introduce siloes and further complicate IAM, leading to misconfigurations and security gaps.
Benefits of Cloud Security Monitoring
Cloud security monitoring provides the following benefits:
Maintain compliance. Monitoring is a requirement for nearly every major regulation, from HIPAA to PCI DSS. Cloud-based organizations must use monitoring tools to avoid compliance violations and costly fees.
Identify vulnerabilities. Automated monitoring solutions can quickly alert IT and security teams about anomalies and help identify patterns that point to risky or malicious behavior. Overall, this brings a deeper level of observability and visibility to cloud environments.
Prevent loss of business. An overlooked security incident can be detrimental and even result in shutting down business operations, leading to a decrease in customer trust and satisfaction — especially if customer data was leaked. Cloud security monitoring can help with business continuity and data security, while avoiding a potentially catastrophic data breach.
Increase security maturity. An organization with a mature infosec model has a proactive, multi-layered approach to security. A cloud monitoring solution enables organizations to include cloud as one of those layers and provides visibility into the overall environment.
Cloud Security Monitoring Challenges
Lack of cloud security strategy. Many organizations hastily migrate to the cloud to support remote work without developing a clear cloud security strategy.
Key stakeholders should know answers to questions such as:
- How can we gain visibility into cloud policy changes or configurations?
- How do we keep track of our assets in the cloud and who has access?
- How will we approach backups? Will we have offsite copies?
- Will our cloud provider have access to company data? If so, what can they do with it?
Without a clear strategy, an organization will not be able to fully reap the benefits of a cloud security monitoring solution.
Alert fatigue. Many cloud monitoring products are noisy, which can result in IT and security teams lacking insight into what’s important to focus on. A FireEye study revealed that some organizations receive up to 10,000 alerts per month from security products. Cloud monitoring solutions with prioritized alerts can reduce the noise and chances of receiving false positives, which provides higher security value.
Lack of context. Logs and alerts are only valuable if an organization understands how to interpret them. Security teams should understand what they want to monitor and why; once they receive alerts, they should know which actions to take. A best-in-class threat detection and response platform will provide remediation steps and playbooks in addition to prioritized alerts.
Cloud Security Monitoring Best Practices
These cloud security monitoring best practices will help you to be strategic, gain visibility into your environment and provide layers of security that will protect against threats:
Carefully evaluate cloud service providers. The big three cloud service providers (Google, Amazon and Microsoft) are fairly comparable when it comes to security. Regardless of the vendor, organizations should evaluate levels of compliance and data/network availability to ensure that it fits their needs.
Perform a cloud infrastructure inventory. Security teams should do a deep dive into their existing cloud infrastructure to understand potential risks, such as shadow IT. Organizations should perform regular audits and know what changes were made within their cloud environments to help identify causes of misconfigurations.
Take a layered approach to cloud security. Setting up layers of security can help organizations to achieve the most visibility into their tech stack. Native cloud monitoring tools such as AWS GuardDuty can help with that, but it’s important to bring in specialized tools to address different components of the tech stack, from physical hardware to orchestration.