Blumira Blog
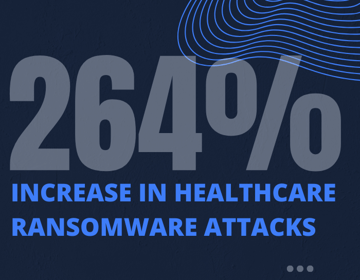
Reducing Risks to Protect Patient Data & Meet HIPAA Compliance
Read More
Blumira’s Kass Lawrence Named to CRN’s 2025 Women of the Channel List
Read More
April 2025 Product Releases
Read More
SocGholish Coming Into Focus for Blumira
Read More
Webinar Recording: How Blumira Does Security Operations
Read More
Building a Better Security Stack: Why MSPs Need a SIEM
Read More
Customer Story: TR Computer Sales
Read More
March 2025 Product Releases
Read More
Blumira's Commitment to MSPs: Q&A with Chris Furner, New Head of Partner Enablement
Read More
Blumira Deepens Commitment to MSP Channel with Comprehensive Program Enhancements
Read More
Customer Story: National Conference of Insurance Guaranty Funds
Read More
Blumira Briefings: Disclosure Drama, Ransomware Breakdown, and MFA Bypass Techniques
Read More
SIEM Starter: A Budget-Friendly SIEM That Meets Compliance & Keeps You Secure
Read More
Introducing Blumira Briefings: Your Weekly Security News Download! 🔔
Read More
Blumira’s MSP Program Earns 5-Star Rating in 2025 CRN Partner Program Guide
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.