Several researchers have released reports that point to the reemergence of IcedID, (aka BokBot), a strain of malware that initially operated as a banking trojan in 2017. Now IcedID has evolved into something far more dangerous: an initial access broker for ransomware threat actors.
The evolution of IcedID from a banking trojan to an initial access broker means that financial institutions are no longer the only target. Any organization that doesn’t have malware prevention in place can be a potential victim.
How Does IcedID Work?
The threat actors behind IcedID typically launch a mass email campaign. Once IcedID has gained a foothold into an environment, the malware threat actors sell that initial access — which often includes reconnaissance intel such as the number of endpoints in the targeted organization, network range, and potential access points — in a cybercriminal marketplace. Ransomware-as-a-service affiliates will purchase the initial access which they use to launch the ransomware attack.
In some campaigns, threat actors use rigged Excel spreadsheets as a delivery mechanism. Threat actors typically use a naming convention that prompts victims to open it, using language such as “refusal,” “claim,” and “overdue.” Users that open the file will see a screen instructing them to enable macros to see the full version.
Once macros are enabled, the malicious formula embedded in the Excel sheet will execute. Malware developers often use white font on a white background to make the formula invisible to victims. Macros on the sheet then download three DLL files with the .dat extension from the command and control servers.
More recent IcedID campaigns involve threat actors using contact forms on legitimate company websites to send emails with malicious links. With this method, the emails that arrive in a victim’s inbox look trustworthy because they are sent using email marketing systems. It’s possible that threat actors have used tools to automate the process and evade CAPTCHA measures, according to Microsoft.
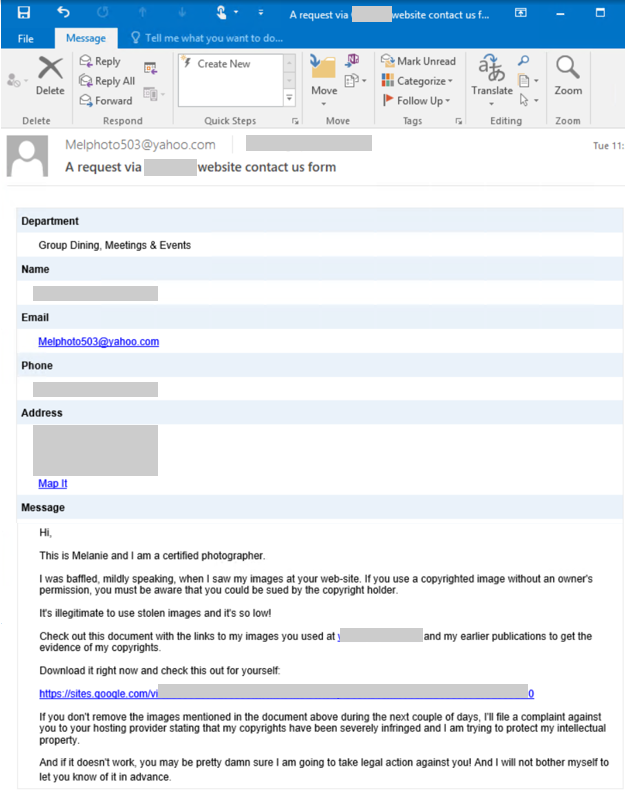
In one particular campaign, the email contained strong language and legal threats about stolen photography, with links to site.google.com for the recipient to view the stolen photos. Once a victim follows the link, which asks them to sign in with Google credentials, the site will automatically download a zip file. This contains a malicious .js file that launches the IcedID attack.
Why Is IcedID Back In 2022?
In 2021, a coalition of eight international law enforcement officials brought down one of the most widespread malware variants, Emotet. Like IcedID, Emotet originated as a banking trojan designed to steal sensitive information. Over the years, however, it morphed into a more sophisticated strain of malware that evaded detection techniques and used command and control servers to receive updates. It eventually became capable of downloading secondary malware payloads, such as “Ryuk” ransomware.
The takedown of arguably one of the biggest players in malware created an opening in the marketplace for cybercriminals to fill — and IcedID is primed to take its place.
IcedID isn’t the only initial access broker for ransomware gangs; other malware families such as TrickBot and Qbot also deliver payloads for ransomware attacks. However, IcedID threat actors have managed to fly under the radar, while strains like TrickBot are heavily monitored by law enforcement.
A few signs have pointed to the rise of IcedID and its use within ransomware attacks. In December 2021, threat actors used IcedID as an initial access vector for Conti ransomware, according to a recent DFIR report. In March 2022, researchers from Intezer discovered a new IcedID campaign that involved conversation hijacking, in which adversaries take over an existing conversation in a victim’s email to spread malware. In this particular “Stolen Image Evidence” campaign, threat actors were sending emails from previously compromised Exchange servers.
Signs of an IcedID Attack
Threat actors have used a few different methods to deploy an IcedID campaign, and as with most cyberattacks, these methods are always evolving — making IcedID more difficult to detect. However, there are a few techniques that have been observed in conjunction with IcedID campaigns:
- Cobalt Strike. Cobalt Strike, a popular command and control (C2) framework used legitimately by pentesters, has been observed in multiple IcedID attacks, and as recently as January 2022, according to eSentire. Researchers at eSentire observed IcedID malware attempting to load Cobalt Strike within 20 minutes of initial infection. In the case of the “Stolen Image Evidence” campaign, adversaries used four different Cobalt Strike servers, which were used to access LSASS memory and perform process injection, among other tasks.
- Use of ISO and DLL Files. IcedID has moved away from office documents, now favoring ISO files with a Windows LNK file and a DLL file, according to Intezer. By using ISO files, threat actors are able to bypass Mark-of-the-Web controls, a security feature that prevents files from performing certain actions. This enables adversaries to execute the malware without warning the user.
- Running built-in Windows utilities. IcedID threat actors also abuse legitimate tools that already exist in an environment, a tactic known as living off the land. For example, threat actors in the “Stolen Image Evidence” campaign used Windows utilities such as net, wmic, chcp, and nltest to perform discovery on the host.
How To Detect An IcedID Attack
Organizations can do a few things to prevent IcedID. Deploying antivirus (AV) software may seem like an obvious first step, but many IcedID campaigns use sophisticated techniques like using a company’s contact forms and legitimate tools to evade detection from many traditional antivirus tools.
Deploy a SIEM with detection and response. A detection and response solution that alerts security and IT teams about suspicious behaviors is typically more effective in preventing sophisticated malware strains like IcedID than antivirus software. Blumira comes with prebuilt detections designed to detect behaviors that are associated with IcedID’s initial access attack path — like running built-in Windows utilities or enabling macros.
A well-tuned SIEM is able to detect these activities because it collects and observes system logs from multiple sources. In many cases, logs indicate attacker behavior earlier in the attack stage, well before malicious tools are introduced into the environment.
Train employees to detect phishing. Nearly every IcedID campaign starts with a phishing email, so employees that are able to detect these emails can prevent an IcedID attack altogether. Security teams can educate employees about phishing in a few ways depending on company culture, such as interactive quizzes, team meetings and casual discussions.
Disable macros. IcedID uses macros to download and execute its payload, so one step that IT and security admins can take is to disable macros for Microsoft Word through GPO, as this will have little to no business impact for most organizations. Enforcing any kind of macro policy for Excel, while recommended, will require more aggressive planning.
Get Started For Free
Not only does Blumira’s threat detection and response solution come with prebuilt detections designed to detect and alert you on suspicious behaviors, but it also comes with a team of real security advisors to help you remediate an issue and take next steps.
Get started with Blumira’s Free edition; in a matter of minutes, you can start detecting and responding to threats in your Microsoft 365 environment. For more coverage and support, it’s easy to upgrade to one of our affordable paid editions.
Erica Mixon
Erica is an award-winning writer, editor and journalist with over ten years of experience in the digital publishing industry. She holds a Bachelor’s degree in writing, literature and publishing from Emerson College. Her foray into technology began at TechTarget, where she provided editorial coverage on a wide variety...
More from the blog
View All Posts
Blumira Joins MES IT Leadership Network: Better Supporting Our Midsize Customers
Read More
Log4Shell Vulnerability: Essential Information
Read More
Nick Brigmon of Blumira on Cybersecurity Insights for Libraries
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.


