Blumira has built an integration with Duo Security, now part of Cisco, to bring a powerful solution to the forefront by providing continuous identity monitoring and automated threat detection and response for organizations of all sizes. You no longer need a fully staffed security team to provide secure remote access for your remote workers – these days, you have enough on your plate, and your IT team is likely stretched to their limits.
By deploying a lightweight software sensor, you can quickly start centralizing logs from all of your security tools and systems onto Blumira’s modern SIEM platform, including Duo’s security logs. Blumira automatically analyzes all security events for potentially suspicious activity so you can better detect and respond to attacks such as ransomware, data exfiltration, brute-force attacks and other indicators of malicious behavior.
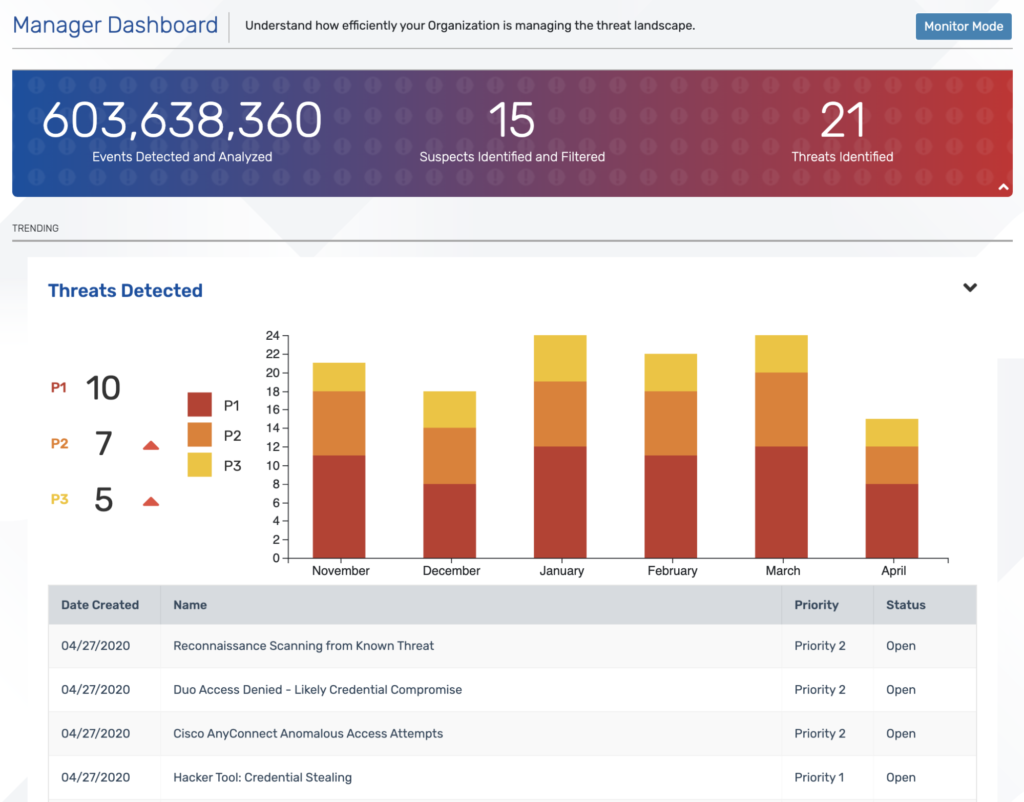
Blumira’s Manager Dashboard shows you detected threats by priority level.
Here’s a few use cases in which Blumira, once set up with Duo, can provide actionable threat detection capabilities, as well as automated playbooks to help customers fully understand the threat and respond to it quickly.
Use Case: User Account Lockout
Blumira can detect Duo user account lockouts – while this may be attributed to user error, it can also occur when an attacker is attempting to brute-force a network asset or launching a Man-in-the-Middle (MitM) attack.
In a brute-force attack, automated software is used to generate a large number of consecutive guesses of a user’s password or personal identification number (PIN) in order to steal the information and gain access to their account. A MitM attack is when an attacker secretly listens in on communications between two parties, with the intent of stealing personal information or gaining access.
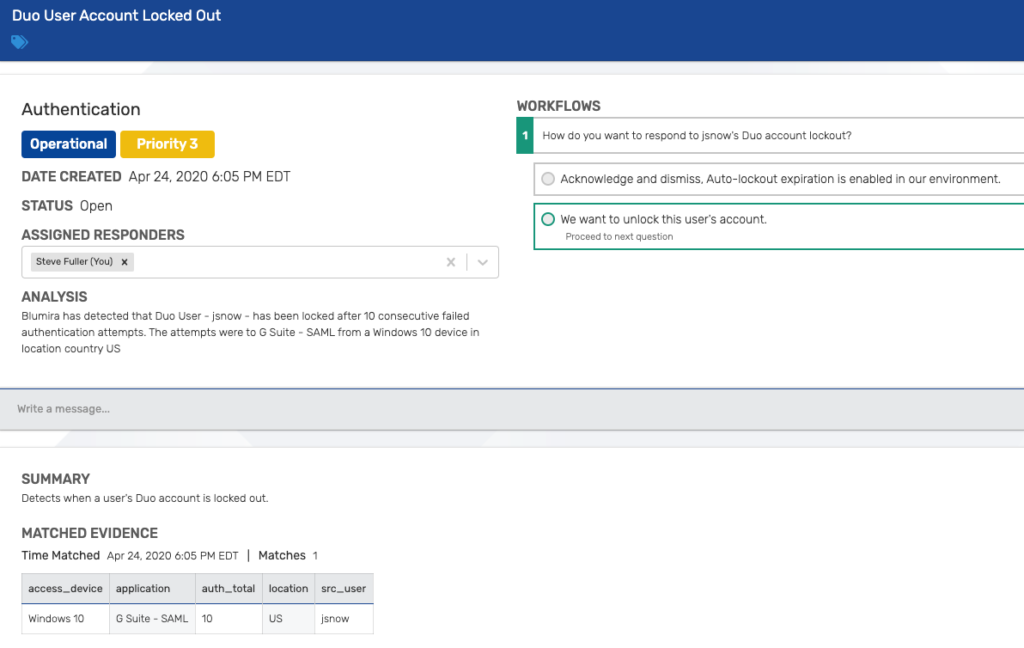
Once alerted to this detection, Blumira gives customers more contextual analysis and a predetermined set of security recommendations to help them make a decision on how to respond. This is known as automated playbooks, or workflows, provided to the customer within our Findings dashboard – an example can be seen below.
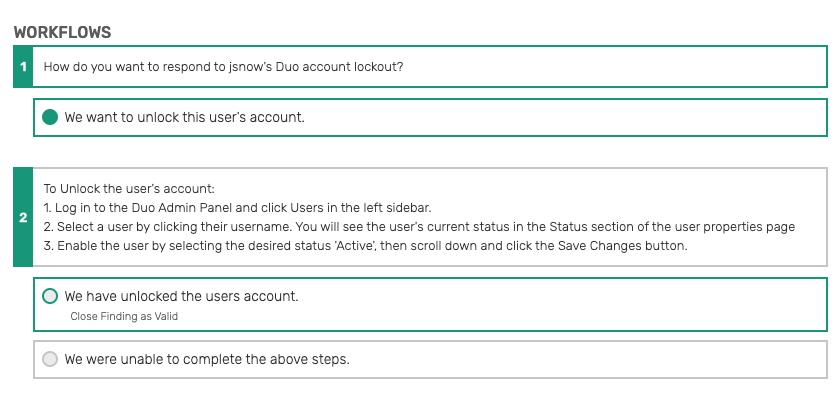
In this example, after detecting a Duo user lockout after 10 failed authentication attempts, Blumira provides a set of options for an administrator, including steps for how to unlock the user’s account.
Use Case: Access Denied – Likely Credential Compromise
In another use case, Blumira can detect a denied Duo access attempt. That means a user has intentionally denied a Duo Push authentication request sent to their phone via their Duo Mobile app. This detection indicates that the user’s primary credentials have likely been stolen, and an attacker is attempting to access your systems through their account.
While Duo blocks access to your systems through two-factor authentication, Blumira can notify your administrators to take action.
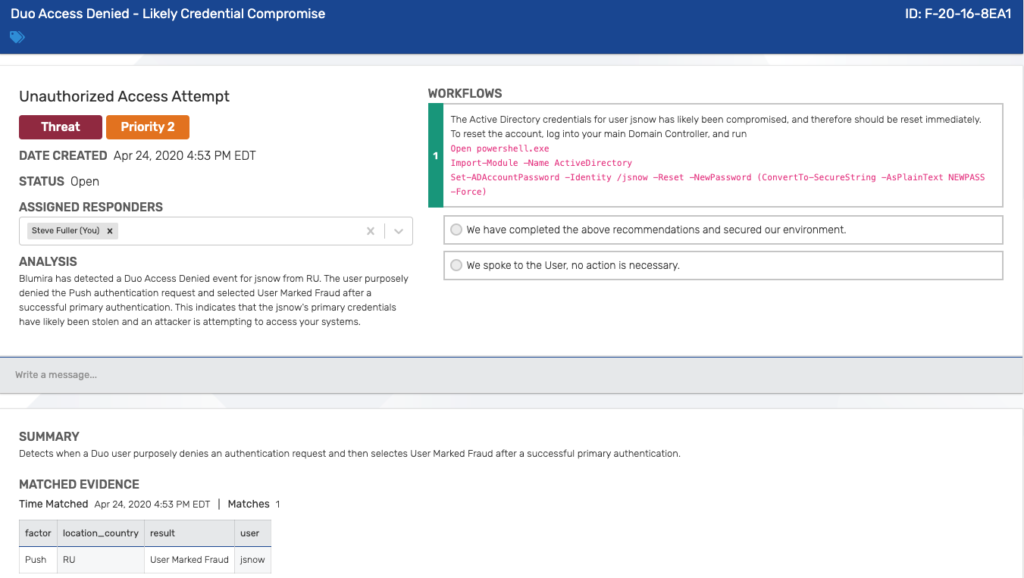
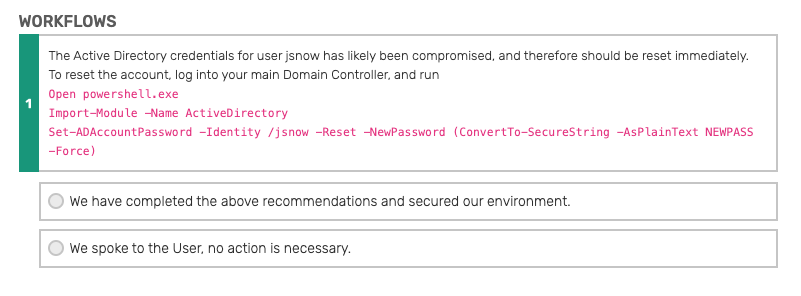
Blumira provides a playbook to walk you through remediation, including security recommendations for resetting user credentials. In this case, the user’s Active Directory password should be reset, and Blumira provides specific instructions on how an administrator can do that, seen below.
Use Case: Password Spraying
Password spraying is when an attacker tries out a few authentications against many users, which is a technique attackers use to avoid triggering brute-force detections or lockout protections put in place by security tools.
Blumira can detect anomalous access attempts, that is, if one or many Duo login prompts have originated from a certain IP address, against a particular user or several users.
This indicates that there’s an increased rate of failure from that particular IP address, meaning that an attacker is likely attempting to gain access through credential reuse or other credential attacks.
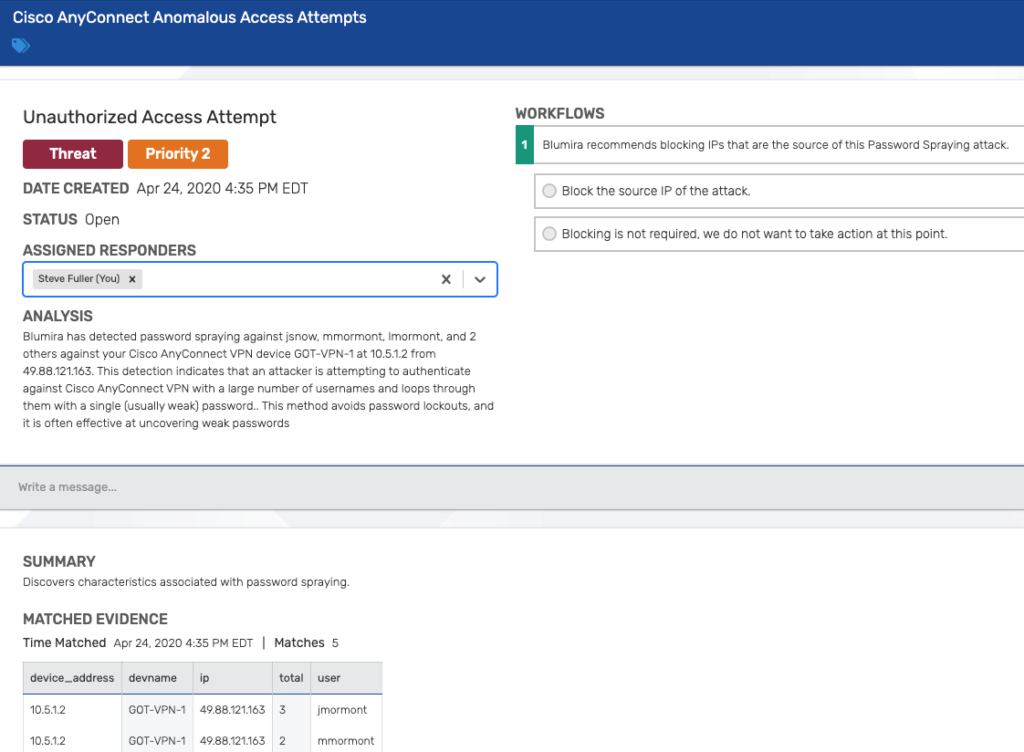
In the example seen above, Blumira can detect anomalous access attempts against a number of users’ Cisco AnyConnect VPN accounts. This indicates that an attacker is attempting to authenticate to your VPN using a password spraying method.
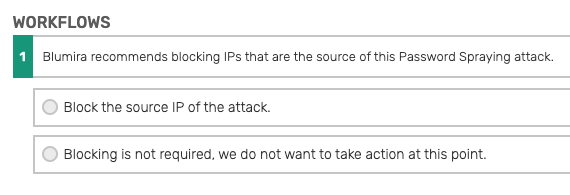
In addition to the threat detection analysis, Blumira provides threat response workflows and recommendations. In this case, we recommend blocking IPs that are the source of the password spraying attack, and then provide a one-click option for administrators to quickly block them.
Modern SIEM: A Force Multiplier
Typical SIEM solutions are complex and require months if not years to set up. Blumira can be set up and running in a matter of hours and days, integrating with your current tools – meaning you can more quickly realize the value of security detection and response.
Plus, traditional SIEMs only aggregate your logs – Blumira is designed to bring you actionable security alerts, then guide you through the act of response and remediation with simplified playbooks that anyone can understand – no need to be a security expert. See the full capabilities of Blumira’s modern SIEM platform, or request a live demo today.
Learn More About Blumira + Duo
- Blumira Integrations: Duo Security – How you can configure the Duo Security service to work with Blumira’s platform using their Admin API.
- Sign up for the Duo + Blumira webinar – Learn about how to achieve better identity and access monitoring with Duo Security and Blumira.
And download “The Modern SIEM Evaluation Guide” to find out how to select a SIEM that meets your security needs without significant overhead.
In this guide, you’ll learn:
- Common challenges with the traditional SIEM approach
- What to expect from a SIEM platform and why it is crucial to your organization’s security strategy
- Key considerations for modern SIEM

 Back to Blog
Back to Blog
