- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
A joint cybersecurity advisory (PDF) was released last week by U.S. agencies informing the healthcare and public health sector of recent ransomware activity (also known as CISA Alert AA20-302A).
In their advisory, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) caution that attackers are targeting the healthcare organization with malware that results in ransomware infection, data theft and disruption of service. They express particular concern for healthcare organizations dealing with cyberthreats during the COVID-19 pandemic, and provide information to help them combat these risks.
It’s Happening: Widespread Ryuk Ransomware Attacks
In September, a Fortune 500 healthcare and hospital services provider, Universal Health Services (UHS) was hit by a Ryuk ransomware attack (BleepingComputer). The disruption caused a shutdown of their business operations and IT infrastructure to contain ransomware spread across their network.
Last week, a medical center in Oregon, a New York-based health system, a Brooklyn hospital and several hospitals within a Vermont health network were hit by Ryuk ransomware. BleepingComputer cites Mandiant’s attribution to a Eastern European hacking group that plans to attack hundreds of other hospitals, while KrebsonSecurity reported on tip that they intend to deploy ransomware at more than 400 other U.S.-based healthcare facilities.
A Closer Look at Ryuk Ransomware
First seen in 2018, Ryuk ransomware infections have been observed as steadily rising since July of this year, attacking 20 organizations per week (Check Point). In 2020, Ryuk is responsible for one-third of all ransomware incidents so far this year, according to statistics from SonicWall’s Capture Labs.
According to the advisory, ransomware attackers will use robust and dual-purpose tools like Cobalt Strike and PowerShell Empire to steal credentials. Cobalt Strike is software that was created for adversary simulations and red team operations, normally used for penetration test engagements – but has also been seen in use for malicious purposes, according to Blumira’s Sr. Incident Detection Engineer Amanda Berlin in Analysis of a Threat: PowerShell Malicious Activity.
Using Mimikatz, a Windows attack tool, this allows them to dump cleartext passwords or hash values from memory. With stolen credentials, attackers can move laterally and map your network to understand the scope of ransomware infection.
From an approach perspective, attackers are using Living off the Land (LotL) techniques to infect healthcare networks. That means that rather than leveraging zero-day exploits, they’re using tools or features that already exist in a target environment to conduct malicious activity. I wrote more about this topic in March – see Top Security Threats: Detecting Ransomware Tactics.
Attackers are leveraging native Windows tools like net view and net computer to locate mapped network shares, domain controllers and active directory. To move laterally, attackers are also relying on native tools, such as PowerShell, Windows Management Instrumentation (WMI) and Remote Desktop Protocol (RDP).
This shows that attackers are not using different or more advanced methods, but rather the same tactics, techniques and procedures (TTPs) that we’ve seen prove to be effective for evading detection and ransomware infection.
Ryuk Ransomware Infection Chain
The advisory details the steps of ransomware infection as follows:
- Attackers send out loaders through phishing campaigns that link to malicious websites or attach the malware to an email message (like TrickBot, BazarLoader or BazarBackdoor)
- Then, loaders distribute the payload, deploy and execute the backdoor from a command & control (C2) server
- Finally, they install malware and/or ransomware on a victim’s machine
Ryuk Ransomware Loaders & Indicators of Compromise
Attackers are leveraging TrickBot tools to deploy ransomware like Ryuk and Conti, and conduct a variety of other malicious activities, including credential harvesting; mail and point-of-sale data exfiltration; and cryptomining.
The FBI reported on new TrickBot modules named Anchor – attackers use anchor_dns, a tool to send and receive stolen data. Anchor evades network defense solutions, blending malicious communications in with legitimate DNS (Domain Name System) traffic by using DNS tunneling.
Attackers have also been seen using BazarLoader/BazarBackdoor. They work together to infect and communicate with the same C2 infrastructure – it’s now one of the most commonly used vectors for ransomware deployment, according to the advisory.
The advisory has detailed code and examples of file, directory and module names to look out for when it comes to TrickBot, BazarLoader and BazarBackdoor. Mandiant also released a list of domains and internet addresses used by a Ryuk threat actor group in previous attacks.
Best Security Practices: Securing Networks From Ryuk Ransomware
U.S. government agencies are advising healthcare organizations to secure their networks by:
- Install patches as soon as updates are released, especially for Windows servers
- Use multi-factor authentication everywhere possible, especially for access to critical applications or services
- Disable the use of remote access or RDP ports and monitor remote access and RDP logs
- Identify open ports and mediate any unnecessary ones
- Audit user accounts with administrative privileges and use the principle of least privilege when configuring access controls
- Audit logs for new account creation to ensure they’re legitimate
Other preparatory actions to take include:
- Prepare network lockdown protocols
- Review incident response plans – maintain copies of data and servers in a separate, secure location
- Identify and back up critical servers, medical records, and infrastructure – keep backups offline from the network
- Set up strategies for redirecting patients in the event of a disruptive attack
- Conduct employee (end user) awareness training on how phishing and ransomware are delivered
Detecting & Responding to Ryuk Ransomware Early
Early detection of attacker tactics and techniques can help you prevent a ransomware infection. Blumira automates detection and response for ransomware prevention and detection by:
Reconnaissance Scanning – By detecting scanning tools on your network, Blumira can identify and alert you to an attacker early in the stages of an attack, before ransomware infection.
Credential Attacks – Blumira detects RDP connections, password spraying, brute-force and more to alert you to attackers attempting to gain access to your network to install ransomware.
Privilege Escalation – Blumira detects whenever administrator-level accounts are added or permissions are changed to alert you to attackers changing privileges in order to move laterally throughout your environment with malicious intent. Blumira can also monitor and alert on account creation.
Data Exfiltration – Attackers are stealing data before infection to use as leverage for demanding a ransom – to prevent data exposure, Blumira detects data exfiltration and any anomalous internal web traffic indicating an attempt to exfiltrate data out of your environment.
Malicious Applications and Files – Blumira detects and notifies your team when an application drops a new file or script on a machine, so you can respond quickly to block or contain malicious executables related to ransomware.
Watch a demo to find out how or contact us to learn more. You can also sign up for a free account of Blumira’s platform to detect and respond to threats in Microsoft 365.
Thu Pham
Thu has over 15 years of experience in the information security and technology industries. Prior to joining Blumira, she held both content and product marketing roles at Duo Security, leading go-to-market (GTM) and messaging for the portfolio solution Cisco Zero Trust. She holds a bachelor of science degree in...
More from the blog
View All Posts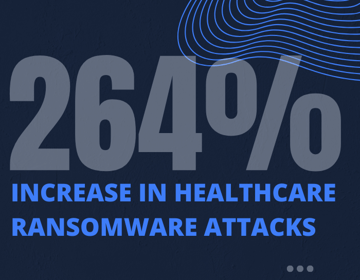
Compliance Security Frameworks and Insurance
5 min read
| May 14, 2025
Reducing Risks to Protect Patient Data & Meet HIPAA Compliance
Read More
Security Trends and Info
4 min read
| April 22, 2024
Ransomware in Healthcare: After-the-Fact is Too Late
Read More
Compliance Security Frameworks and Insurance
6 min read
| February 22, 2024
Using the NIST CSF to Support GDPR and HIPAA Compliance
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.
 Click to Enlarge
Click to Enlarge