- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
Investigating security findings often means digging through dense data logs, switching between dashboards, and trying to make sense of technical data. The process is time-consuming, slowing response times and creating unnecessary friction for IT teams. Even with all that effort, analysts still lack a complete picture of activity across their environment, making it harder to connect the dots. Without the right context, alerts take longer to resolve and senior staff are pulled into issues that should be routine.
Introducing SOC Auto-Focus
SOC Auto-Focus accelerates your security investigations by using AI-powered analysis to enrich Blumira findings with plain-language summaries and guided investigation steps. It analyzes evidence from new findings, compiles relevant data from across your environment, and presents it all in a digestible format to support your team's decision-making process.
Instead of starting from scratch, your team immediately sees the full picture with what happened, why it matters, and how to respond, helping analysts of any skill level respond faster and with confidence. In addition to prioritizing details from the finding, Auto-Focus maps suspect activity to recognized attack patterns and provides better context on why it presents a risk. Auto-Focus doesn’t replace your team's judgment; it gives them the context they need to make better decisions faster. It also makes Blumira’s built-in expertise more accessible than ever, helping augment your team’s existing security knowledge with our guidance.
When a new finding appears in Blumira, SOC Auto-Focus immediately analyzes the log details and enriches them with expert-driven context:
- Instant Context: A plain-language summary that highlights the most important details up front.
- Clear Prioritization: Each finding includes a criticality rating, recommended response timeframe, and confidence score so your team can focus on the most important alerts.
- Guided Response: Step-by-step investigation and remediation actions appear right on the Findings page, based on Blumira’s proven security workflows mapped to MITRE ATT&CK patterns.
- Security Education: Each recommendation explains the reasoning behind it, giving analysts in-the-moment training that builds expertise over time.
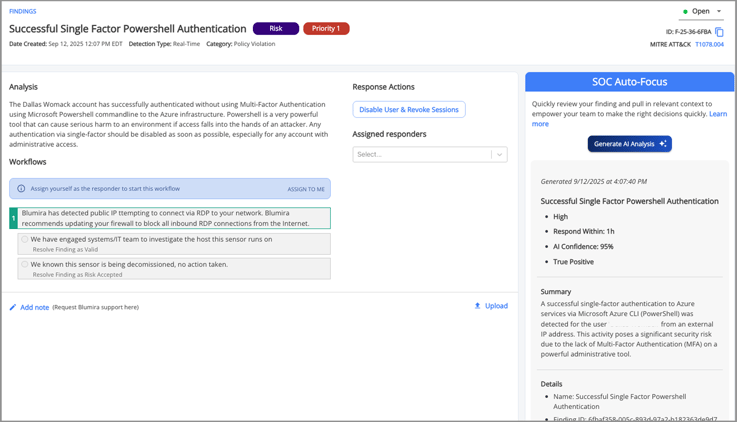
Example of SOC Auto-Focus on Findings page
How it Works
SOC Auto-Focus is available for Automate customers Once analyzed, results from analysis are shared across all users in the organization and stored indefinitely for reference. This feature includes usage parameters to ensure analysts have actionable, repeatable guidance without introducing noise or redundancy:
- A finding can be analyzed once every six hours
- After an analysis is generated, a cooldown applies before the same finding can be re-analyzed, during which the window will display “Waiting for cooldown.”
- Your organization is allocated 10 analyses per month, plus 1 additional run for every 5 employees.
How Our Partners are Using SOC Auto-Focus
NineStar Connect, a community-based utility cooperative and MSP, uses SOC Auto-Focus to cut investigation time in half by reducing manual log review and context switching for complex alerts.
“Auto-Focus translates technical alerts into plain language summaries and points me directly to the impact. It bridges the knowledge gap instantly, saving me from spending time digging through logs or Googling for answers.”
Travis Short, SOC Analyst, NineStar Connect
By surfacing direct links to the right resources and translating technical details into human-readable content, Auto-Focus has become both a shortcut and a force multiplier for NineStar Connect’s SOC team. The result: faster investigations, improved confidence, and more consistent outcomes.
Read the full customer story to see how NineStar Connect uses Auto-Focus to accelerate investigations and boost analyst confidence.
See SOC Auto-Focus in Action
SOC Auto-Focus is now available for Automate customers. By delivering plain-language findings and guided response steps, Auto-Focus helps your team investigate faster, reduce workload, and build confidence in every decision.
For many security teams, the difference between quick, confident investigations and drawn-out ones comes down to context. SOC Auto-Focus puts that context directly in the Findings page, so analysts of any level can act faster and more effectively.
Request a demo of Blumira Automate to see how SOC Auto-Focus can transform your investigations.
Eric Pitt
Eric is a Product Marketing Manager at Blumira focusing on customer research and positioning to continuously improve the Blumira platform.
More from the blog
View All Posts
Blumira News
15 min read
| August 30, 2022
Now Available From Blumira: MSP Portal!
Read More
MSP
5 min read
| June 21, 2022
3 Steps For MSPs To Sell Blumira’s SIEM: From NFR to Standard Offering
Read More
Customer Success Stories
5 min read
| October 15, 2025
Customer Story: NineStar Connect Cuts Alert Resolution Time in Half with SOC Auto-Focus
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.