The 2021 edition of Verizon’s Data Breach Investigations Report (DBIR) highlighted the rise of ransomware and the importance of security monitoring, among other key cybersecurity trends.
Ransomware On The Rise
Verizon reported another increase in ransomware cases, which has been trending upward since 2016. Ransomware now accounts for 5% of total incidents that Verizon reported, and 10% all of breaches.
“This is because actors have adopted the new tactic of stealing the data and publishing it instead of just encrypting it,” the report reads.

The financial motivation of organized crime continues to be the biggest threat actor category for organizations. Blumira has similarly identified this pattern across organizations it protects — not only in ransomware attack attempts but also cryptominer worms and other threats that are focused on generating revenue for attackers.
While Solarwinds and supply chain attacks are visible and scary, they aren’t what is likely to impact organizations. As the world grows in turmoil and inequality escalates with it, so does the ability to earn money from victims.
While the majority of organizations in the report had no vulnerabilities, random sampling shows older vulnerabilities continue to be a thorn in the side of organizations.
Understanding your attack surface by identifying what you’re exposing, how it’s being interacted with, and building a strategic plan to reduce these is paramount. As organized crime grows its reach deeper into ransomware (10% increase YoY), these vulnerabilities act as continued target vectors for groups to build their bank further. Of course, patching vulnerabilities if they impact your environment is the highest priority, but it’s also important to have a strategic plan that focuses on reducing risk and impact.
Stages of The Kill Chain
The Verizon report also highlighted the frequency of attack stages during the beginning, middle and end of a breach. Hacking and errors were the most common actions at the beginning of a breach, then malware and hacking became more common later on in the attack once the actor gained an initial foothold.
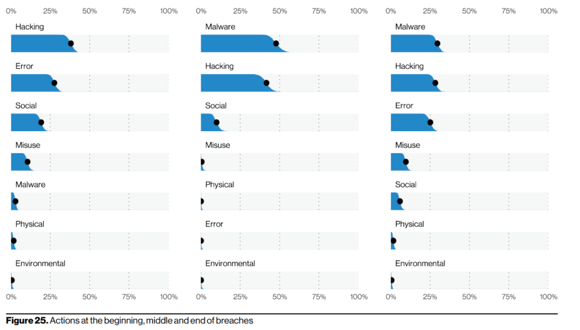
This further illustrates the need to have precise detections with robust recommendations for data gathering that do not necessarily depend on a specific technology to exist.
IT and security teams are more likely to be successful at stopping the attack when they identify the patterns that are associated with hacking and malware at each stage, rather than depending on a specific AV provider to have a complex AI process to identify a new weaponized file.
A threat detection and response solution like Blumira’s will detect and alert you about early patterns associated with malicious behavior like hacking and malware, such as SMB and RDP connections from public IP addresses.
Incorporate Security Training Into Company Culture
The report showed that the larger the organization, the greater chance that it will be impacted by large scale phishing or broad social engineering attacks.

The report also showed that the majority of social engineering incidents were discovered externally.
“This means that when employees are falling for the bait, they don’t realize they’ve been hooked. Either that, or they don’t have an easy way to raise a red flag and let someone know they might have become a victim,” the report reads.
This highlights the importance of security awareness training. It’s also important to ensure that there is no culture of blame and that users are reinforced with explanations of what to do next time.
Business email compromise (BEC) was the second most common form of social attacks, according to Verizon, and it is continuing to increase. The median loss associated with BECs was $30,000, with 95% of BECs costing between $250 and $984,855.
Again, internal training is a must to prevent BEC.
However if you’re quick, you can generally freeze and recover most losses for BEC, something Blumira has also observed. Recovery of BEC rates — in addition to organizations not reporting losses from ransomware — shows that organizations may be pulling back on ransomware payments, are able to recover more readily, and are combating organized crime more as it grows in prevalence.
How Blumira Can Help
Blumira’s cloud threat detection and response solution alerts your team about suspicious behavior that leads to security incidents, like malware and ransomware infections — and provides recommendations on next steps. Test it out with a free trial.
Matthew Warner
Matthew Warner is Chief Technology Officer (CTO) and co-founder of Blumira. Matt brings nearly two decades of IT and cybersecurity experience to his leadership position, and a genuine passion for cybersecurity education. Prior to founding Blumira, he was Director of Security Services at NetWorks Group, a managed...
More from the blog
View All Posts
Blumira Expands Its Cloud Security Coverage With AWS Security Monitoring
Read More
Detect & Prevent Infection: 50% Rise in Ransomware Attacks
Read More
Duo + Blumira: Identity, Monitoring & Threat Detection
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.