Windows RDP (Remote Desktop Protocol) allows for convenient remote access connections to desktops and servers and is very useful for IT teams to manage their infrastructure. Since the global covid-19 pandemic has ushered in a rise in remote working, we’ve taken a look at our honeypots to see if there has been any change in patterns from RDP attacks.
A honeypot is designed to replicate real systems and lure attackers to log in – once this activity is detected, it can send an alert to an IT or security team. This provides visibility into malicious activity, alerting you to attackers’ attempted lateral movement. Blumira provides easy-to-setup and configure honeypots for our customers.
For our internal security, Blumira maintains a number of servers that sit in the cloud around the U.S./globally that allow for risky actions and are logged out. This is largely for our own internal visibility and threat feeds, but more importantly, it gives Blumira the ability to watch patterns of attacks such as attacks against RDP servers, listening on the internet.
If a successful authentication occurs, you will more than likely be hit with ransomware – this is one of the most common ways that organizations get infected by ransomware, outside of phishing attempts. Ransomware is likely the best case result – as at least your organization will be aware of the breach, whereas lateral exploitation and exfiltration of data within your environment could result in exposure of all intellectual property and internal data, not just loss.
A few quick facts about RDP:
- “Remote administration tools, such as Remote Desktop Protocol (RDP), as an attack vector have been on the rise since mid-late 2016 with the rise of dark markets selling RDP Access.” (U.S. Dept. of Homeland Security)
- Buying RDP login credentials (often stolen or accrued via brute forced attacks) is easy and inexpensive on cybercrime marketplaces – they can go for $20 each on the dark web (BankInfoSecurity)
- Attackers with direct RDP access to your environment can infiltrate and infect your systems with ransomware, a very big and lucrative business – estimated at $20 billion by 2021 (SafetyDetectives)
RDP Attack Trends: Up Since the 2020 COVID Pandemic
So what did we find after pulling and analyzing Blumira’s honeypot data? The data below spans the time period from the end of 2019 to May 7, 2020, showing the trend changes over the COVID-19 realizations in the world impacting attacks on internet-facing assets.
Click Above to Enlarge
Blumira Honeypot Data Summary
Our findings are based on 900MB of data, showing remote desktop protocol attack movements against a honeypot hosted by Blumira within the GCP (Google Cloud Platform) infrastructure. We pulled over eight million records containing time of authentication, source IP, source countries, and the user they attempted to authenticate with for each access attempt.
We found:
- There were 179,085 different usernames attempted from 7,073 distinct IPs, from at least 122 countries of origin
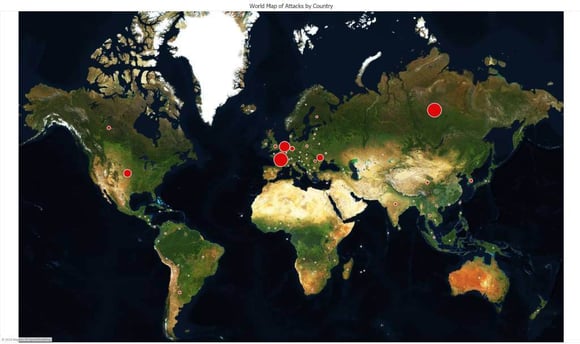
- Two million attacks against our RDP honeypot originated from Russia
- Another 2 million originated from France, followed by 1 million from the Netherlands and U.S.
- A very significant increase from December 2019 to April 2020 – attacks rose 85% over time
Click Above to Enlarge
We also saw significant spikes in attacks across the month of April across all scanning and brute-force login attempts, which is evident in the RDP session attacks seen against our honeypot. At the end of April, we saw nearly 1.5 million attacks, an 85% change over the time periods seen below:
Click Above to Enlarge
This is a significant increase from the end of December, where we saw around 15,000 attacks on the same honeypot. A point-in-time comparison shows a 9,769% increase since the end of December 2019 to the end of April 2020.
Protecting Against RDP & Ransomware
Using RDP over the internet exposes your environment to attack, but also potentially exposes the connection to being stolen and your entire session replayed offline. GoSecure provides a great overview of RDP man-in-the-middle (MiTM) attacks.
Here’s a few of our security recommendations regarding RDP:
- It should be noted that RDP should never be internet connected, as it is not a secure method of remote management.
- RDP, typically over TCP port 3389, is not secure in general without configuring Network Level Authentication (NLA) and similar protections.
- Any and all remote access should flow through a proper virtual private network (VPN) connection protected by multi factor authentication (mFA) whenever possible, and use strong passwords.
- Limit the number of users that need RDP access and limit access to specific IPs, whenever possible to follow least privilege principles (see tips on Group Policy Management).
In cases that RDP is facing the internet, you should expect to see the above attacks on a constant basis.
How Blumira Helps Detect & Respond
Blumira has a number of detections that focus on risky connections from the internet. Some may amount to risk for the environment, such as FTP (File Transfer Protocol) connections from the internet, and some, like RDP connections, are legitimate threats to the environment and should be acted on within a few days when detected. Blumira categorizes these as a Priority 3 Threat.
As you can see below, when this detection is applied to the honeypot, within 15 minutes, we see a significant detection associated with connections from the outside. This along with FTP, SMB (Server Message Block), SFTP (SSH File Transfer Protocol), and others allows for broad detection of risks and threats against an environment from the outside world.

Click Above to Enlarge
In the playbook/workflow steps listed above, we recommend that the connecting IP addresses are blocked immediately, and the target server is taken off of the public-facing internet. You can do this easily within Blumira’s platform in one click through Blumira’s Dynamic Blocklist feature that blocks all source IPs for the next seven days.
Webinar: Protecting Against the Rise in Remote Access Attacks

Join me as I discuss our findings and more about how Blumira can help detect and protect against these types of attacks in our upcoming webinar, Protecting Against the Rise in Remote Access Attacks on June 2, 1pm ET | 10am PT.
Learn More
What is a Honeypot? (Video)
Honeypots are an effective security measure that can be used to detect lateral movement and potential threat actors on your network. Blumira makes it easy to deploy and manage honeypots with low effort, allowing for early detection of attacks and threats.
Hands in the Honeypot: Detecting Real Security Threats
What is a honeypot? Here’s how to set up a honeypot with Blumira to help you detect and stop network intruders.
Matthew Warner
Matthew Warner is Chief Technology Officer (CTO) and co-founder of Blumira. Matt brings nearly two decades of IT and cybersecurity experience to his leadership position, and a genuine passion for cybersecurity education. Prior to founding Blumira, he was Director of Security Services at NetWorks Group, a managed...
More from the blog
View All Posts
An Analysis of the Most Active Ransomware Variants
Read MoreHow Manufacturers Can Secure Themselves Against Cyber Threats
Read More
Shortening Ransomware Dwell Time Requires Fast Detection
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.