Microsoft Exchange vulnerabilities affected many organizations, but some fared better than others with the help of trusted security advisors.
Fechheimer, a global uniform manufacturing company, was one organization affected by the Exchange vulnerabilities. Fortunately, Fechheimer was able to successfully evade a major security incident with the help of Blumira’s security team.
Here’s how it unfolded.
Blumira Team Sends Security Email
On March 2, Microsoft released zero-day patches for vulnerable Exchange servers actively being exploited by China-based attacker group, HAFNIUM, on Patch Tuesday.
In response to Microsoft’s announcement, Mike Behrmann, Director of Security at Blumira, sent out a security email to all Blumira customers. In the email, he explained what usually happens when zero-day exploits are publicly disposed and patches are released. He also provided recommendations for next steps.

Fechheimer Engages With Blumira
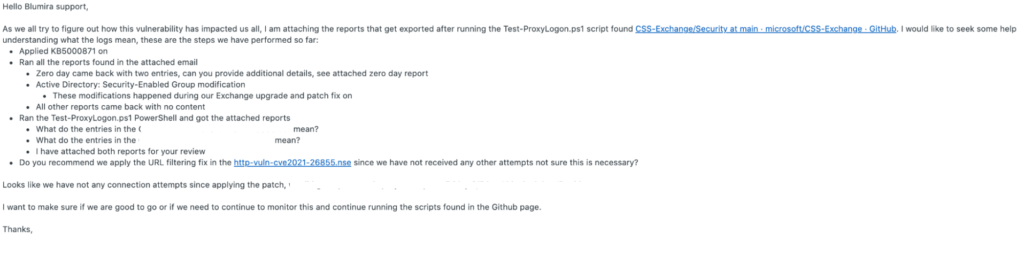
Members of Fechheimer’s IT team submitted a Support ticket to Blumira requesting that Blumira review their HAFNIUM remediation plan. They had performed the recommended Microsoft patch to their Exchange server immediately after they were made aware of the zero-day vulnerabilities, but it was unclear whether the server was impacted before the zero-day patch was applied or if the patch was applied successfully.
Fechheimer was seeking validation that their Exchange server was safe.
Blumira Recognizes Potential Security Incident
Mike Behrmann spotted a C2 (command and control) finding for Fechheimer later that night. Based on the C2 traffic and the diagnostic script output, Mike became extremely concerned that Fechheimer had been attacked. 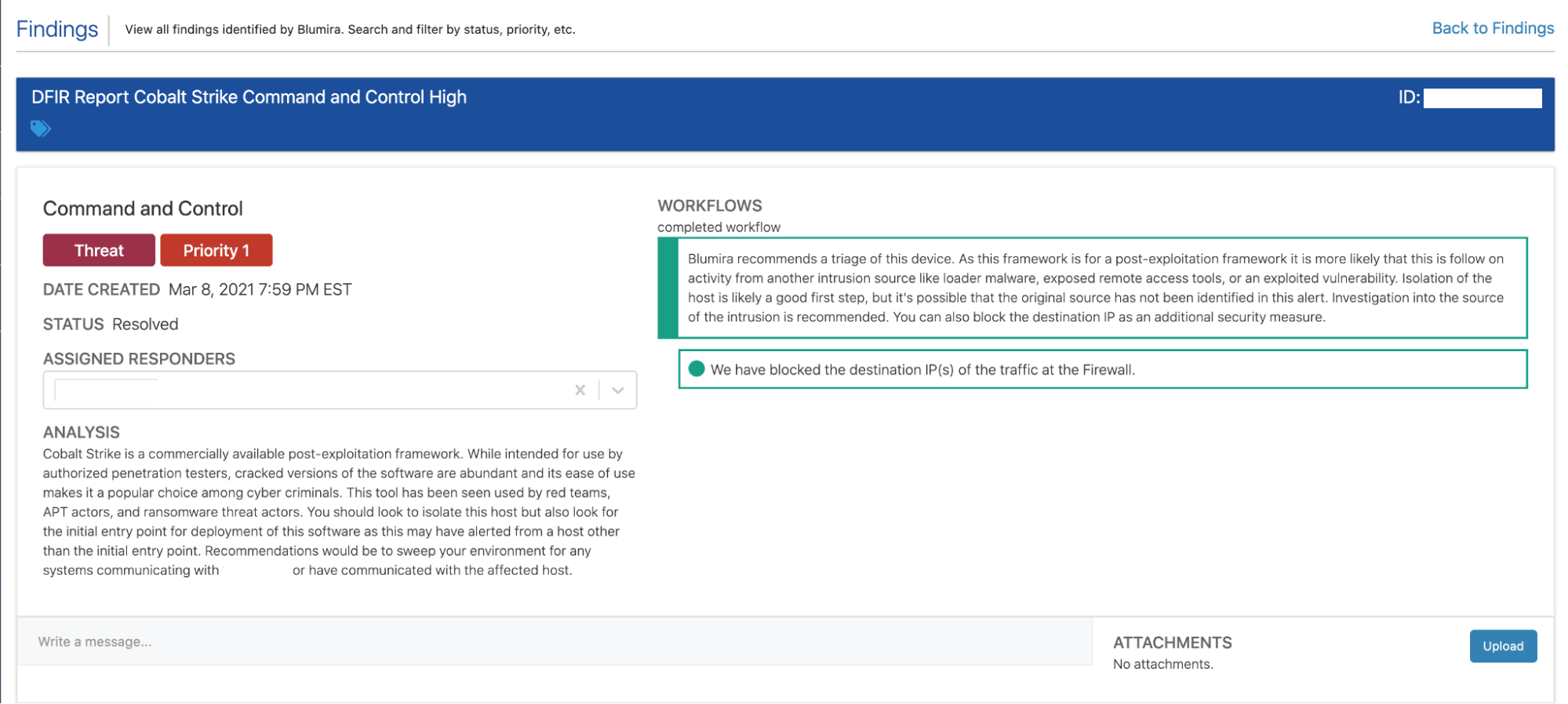
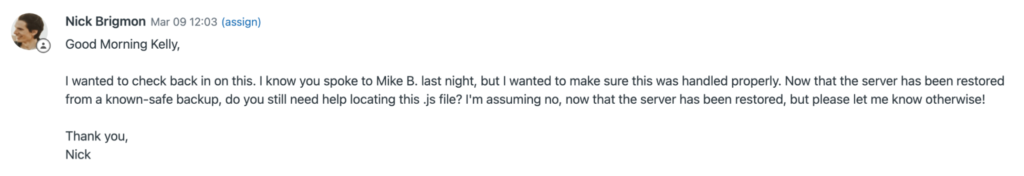
Blumira’s security team confirmed the output of the Test-ProxyLogon.ps1 diagnostic script. Mike made contact with one of the primary points of contact at Fechheimer. He explained the gravity of the security situation and urged Fechheimer’s IT team to contain the server by disconnecting it from the local area network. Mike also offered specific reconstruction options, like restoring from a trusted backup or rebuilding the server from scratch.
Out of an abundance of caution, Fechheimer’s IT team took immediate action and opted to restore from a trusted backup.
Blumira Confirms Fechheimer’s Success
The next morning, Blumira’s Incident Detection Engineer, Nick Brigmon, followed up with Fechheimer’s IT team to check on their progress. Fechheimer’s team confirmed that they were able to restore from a known-safe backup and that the server was fully patched.
“Blumira did a great job of alerting us to a Cobalt Strike command on our recently patched server. Without their alert, it may have been some time before we knew it was residing on the server. This is what is so scary about zero-day exploits,” said Steve Gatton, VP of Information Technology at Fechheimer.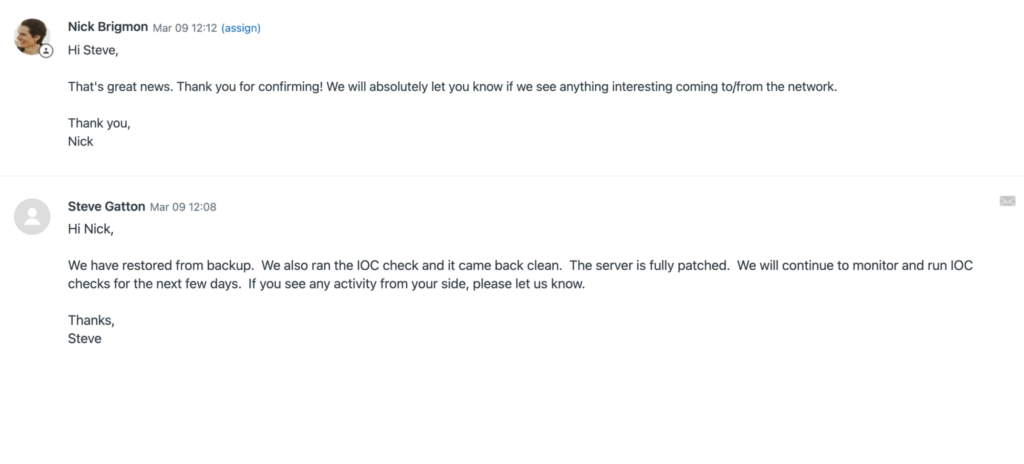
Relying on Blumira’s Trusted Security Advisors
Alerts can help uncover security incidents, but only if IT teams know how to interpret and respond to them. That’s where Blumira’s security advisors come in.
Blumira’s security team helps customers protect themselves against cyberattacks by:
- Proactively alerting customers to major vulnerabilities
- Interpreting customers’ vulnerability diagnostic script results
- Proactively reaching out after a concerning finding and offering incident response guidance
- Following up about progress and addressing any remaining customer concerns
Blumira’s cloud SIEM integrates with Microsoft Windows servers to collect event logs, analyze activity for indications of attack patterns, then alerts your team with a high confidence of a real ongoing threat. Our security playbooks give you the next steps to respond quickly and contain the impact of a threat. Our security team can also provide proactive guidance to help advise you on remediation.
To see how Blumira’s security team can help your organization, try our free trial.
Read More: Learn How Blumira Detected Another Exchange Attack

 Back to Blog
Back to Blog