Compliance Security Frameworks and Insurance
The Iranian Cyber Threat: Key Insights for IT Teams
Although there is currently a ceasefire in place, geopolitical tensions between the United States and Iran continue to escalate. As a result, we're witnessing a corresponding...
Read More
Customer Story: United Way of Pierce County
Read More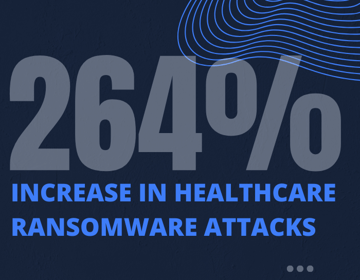
Reducing Risks to Protect Patient Data & Meet HIPAA Compliance
Read More
NIST Cybersecurity Framework Implementation for Mid-Market Companies: 2025 Update
Read MoreVideo - Security Monitoring Essentials for 2025 Compliance
Read MoreMeeting Florida's 2025 Cybersecurity Deadline: Funding and Compliance
Read More
State of Florida Cybersecurity: Local Governments Must Comply by Jan. 1, 2025
Read More
Customer Story: Erinapp
Read MoreNavigating the FTC Safeguards Rule: A Guide for Auto Dealerships
Read More4 key steps to building an incident response plan
Read MoreTips to combat the rising costs of cyber insurance
Read More
A Guide to Compliance for State and Local Governments
Read More
10 Steps to ISO 27001 Certification for Your Manufacturing Company
Read More
Compliance Conundrum: Does Cybersecurity Hinder Credit Union Progress?
Read More
Customer Story: Midway Swiss Turn
Read More
Customer Story: Republic Electric Company
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.
