Small and mid-sized businesses (SMBs) are a prime target for cyber threats due to a lack of budget, resources or general awareness of security best practices that can leave them defenseless and without visibility into what’s going on across their network – especially when it comes to using cloud applications and remote access tools.
A study of managed service providers (MSPs) found that 91% of reported attacks against SMBs over the last two years were attributed to ransomware.
SMB cybersecurity can’t be an afterthought, especially as attackers increasingly target resource-strapped teams.
Security information and event management (SIEM) platforms can detect suspicious behavior that leads to breaches and ransomware, reducing security risk. But traditional SIEM products are often too complex and expensive for small teams.
Fortunately, there are options for small businesses to find a SIEM that’s the right fit.
SIEM Challenges For Small Businesses
These are some of the main issues with managing your own security team – or the lack thereof:
1. Balancing IT and Security Tasks
Many security teams have also been pushed to take on an increase in IT-related tasks to support a remote workforce. A recent International Information System Security Certification Consortium (ISC)² survey found that nearly 50% of security professionals have been temporarily taken off of security duties to assist with IT tasks, such as supporting a mobile workforce.
Yet the survey also revealed 23% of security professionals said that security incidents experienced by their organization have increased since transitioning to remote work, with some citing double the amount of incidents.
2. Full-Time Security is Too Resource-Intensive
Many organizations don’t have the funding to invest in in-house security talent to deploy and manage traditional SIEM tools that centralize logs across your environment to help you detect malicious activity. Typical SIEMs only aggregate your logs, doing little to no analysis and serving up a flood of alerts to your IT and security teams.
That means in addition to running a SIEM, you’d also have to staff a security operations center (SOC) with security engineers that monitor your logs 24/7 for any indicators of a potential compromise. Once you’ve prioritized which alerts are worth following up on, you’d have to enlist the services of analysts to investigate and remediate.
3. Security is Too Slow
The entire process from detection to investigation and remediation can be too slow and manual for most organizations to stay ahead of both insider and evolving external threats. Without an entire team of analysts continuously monitoring and writing new threat detection rules, you can fall behind. Plus, there are other initiatives your team needs to focus on, including innovating on your core business.
4. Difficulty in Hiring Security Talent
Statistics place the number of unfilled information security positions at 1.8 million by year 2022, but that may be due to a number of factors as outlined by DarkReading – including mismatched expectations for salaries/experience, the amount of training required, and the role employers have when it comes to looking for candidates with experience outside of typical technical and/or security backgrounds. Whatever the reason is, security remains a difficult field for talent acquisition for all types of organizations in this current global climate.
Choosing a SIEM For Small Businesses
Without a fully-staffed security team and the resources to maintain a legacy SIEM, can you still quickly detect, investigate and analyze threats? As well as automate response and remediation – all in one streamlined platform?
Replace Legacy SIEMs
Most standalone SIEMs (often acquired to meet compliance requirements) cannot provide enough security value to justify their cost, and are complex and time-consuming for security/IT teams to fully operationalize. By replacing legacy SIEMs with a single streamlined platform like Blumira’s modern SIEM that automates the more manual aspects of threat detection and response, you can take the burden off of your small team and better optimize their time.
Consolidate Security Spend
Make the most of every investment and reconsider how many security tools you need in your arsenal. Consolidate spend and get only the most critical capabilities of a SIEM; security orchestration, automation and response (SOAR); and a security operations center (SOC) – all built into one automated platform. Most SIEMs require additional security products layered on top for threat detection, investigation and remediation.
End-to-End Threat Detection & Response
Make your security platform work harder for you – Blumira’s modern SIEM automates and integrates:
Advanced Threat Detection – Blumira correlates and analyzes security events with dozens of threat feeds to pick up on indicators of suspicious activity or potential threats.
Automated Threat Response – Your organization can block threats immediately with dynamic blocklists delivered through Blumira’s firewall integrations, meaning once a threat is detected, you can configure the platform to block the IP address it’s originating from.
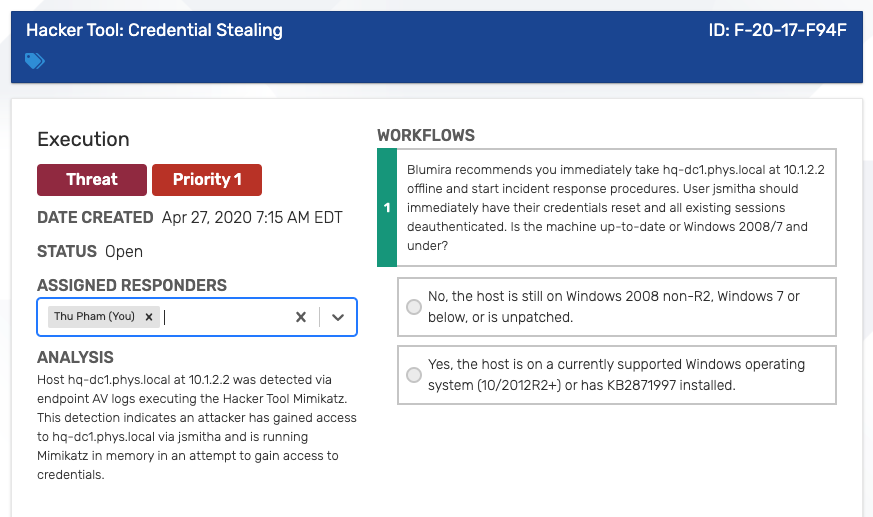
Guided Security Playbooks – Once Blumira detects a threat, our platform provides an analysis, any matched evidence (specific users affected, IP addresses, regions, URL paths, etc.) and step-by-step workflows that walk your team through remediation and response.
Virtual Honeypots – In addition to the capabilities of investigating and remediating all through one tool, you can get the benefits of threat detection with the help of a honeypot that’s easy to set up and configure through Blumira. Watch our video or read our blog post to learn more about how honeypots work.
Reports for Compliance – Blumira guides you through the process to get access to the data and reporting that you need to help you investigate, report and meet compliance requirements such as PCI DSS, FFIEC, NIST 800-53, HIPAA and other compliance frameworks.
Case Study: Replacing Traditional SIEM With Blumira
To realize the full benefits of what Blumira provides, Greenleaf Hospitality CIO Michael Cross reflected:
“Greenleaf would have to hire full-time people in a very specialized field, with a fully loaded salary. But the biggest costs are in the intangibles; the human capital costs of training, hiring and attrition.”
Prior to partnering with Blumira, Greenleaf contracted with a large SIEM provider. Unfortunately, Greenleaf’s IT team was flooded with alerts. Greenleaf determined that Blumira’s security expertise was critical in identifying only the most important events and avoiding alert fatigue. Cross credits Blumira with a strong understanding of Greenleaf’s environment, as well as deep expertise in security and managed services.
“When we came on board, we assessed our needs and it became clear that there was a level of skill set that we needed to properly manage and secure our environment that we weren’t able to fill with our internal team. Good security engineers are very expensive.”
Read the complete Greenleaf Hospitality case study.

 Back to Blog
Back to Blog